Security: SASE with ZTNA
As a first step, we perform a FREE security assessment. Azure AD, Microsoft 365, Sharepoint Online, Teams, local servers (AD) and workstations are under scrutiny. This allows us to propose a fact-based action plan: according to the degree of risk, we draw up a list of priorities. In this way you can show your customers that you take security seriously and that you are building compliance.
SASE: Secure Access Service Edge
Approach
We base our approach on Secure Access Service Edge, often abbreviated to SASE. It is a security framework that combines SD-WAN (Software-Defined Wide Area Networking) and Zero Trust security solutions into a converged cloud platform that connects users, systems, endpoints and external networks with apps and users. We work with solutions from vendors such as Barracuda, Cisco Meraki and Microsoft.
Main goal
The main goal of SASE architecture is to provide a seamless user experience, optimal connectivity, and comprehensive security in a way that supports the dynamic security needs of digital enterprises. Rather than bringing traffic back to traditional data centers or private networks for security inspections, SASE ensures that devices and remote systems can seamlessly access apps and resources at any time, wherever they are located.
![]()
An SD-WAN (Software-Defined Wide Area Network) is an overlay architecture that uses routing or transmission software to create virtual connections between both physical and logical ones. SD-WANs provide virtually unlimited paths for user traffic. This optimizes the user experience and enables powerful flexibility in encryption and policy management.
![]()
FWaaS (Firewall as a Service) moves firewall security to the cloud instead of the traditional network perimeter. This allows organizations to securely connect remote, mobile workers to the corporate network while still consistently enforcing policies that extend beyond the organization’s geographic footprint.
![]()
ZTNA (Zero Trust Network Access) is a set of consolidated cloud-based technologies. They operate in a framework where trust is never implicit and access is granted to the users, devices and applications on a need-to-know basis. In this model, all users must be authenticated, authorized, and continuously validated before gaining access to personal corporate applications and data. ZTNA eliminates the poor user experience, operational complexity, costs and risks of a traditional VPN. You can read more details below under the heading Zero-Trust principles
![]()
A CASB (Cloud Access Security Broker) is a SaaS application that acts as a security checkpoint between on-premises networks and cloud-based applications. In addition, it enforces security policies. A CASB protects corporate data through a combination of prevention, monitoring, and recovery techniques. It can also identify malicious behavior and alert administrators of compliance violations.
![]()
A modernSASEplatform enables IT administrators to manageSD-WAN, SWG, CASB, FWaaSandZTNA through centralized and unified management in different networks and security. This allows IT team members to better focus on more pressing matters, and improves the user experience for hybrid workers in the organization.
- Reduced IT costs and complexity
- Greater flexibility and scalability
- Built to support hybrid work
- Better user experience
- Improved security
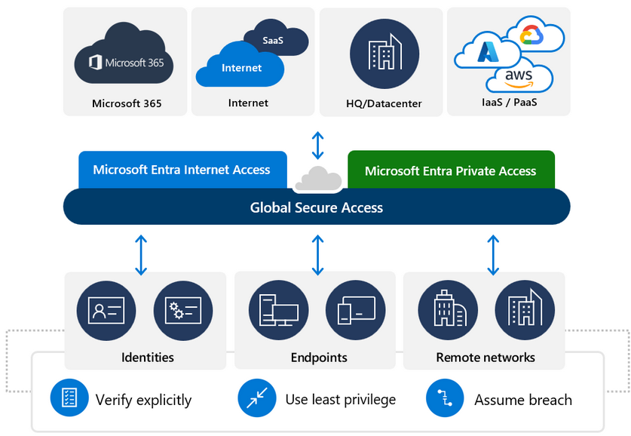
Zero-Trust principles
Instead of assuming that everything behind the corporate firewall is safe, the Zero Trust model assumes there is a breach and authenticates every request as if it were coming from an open network. Regardless of where the request comes from or what source it consults, Zero Trust teaches us to “never trust, always verify.” Each access request is fully authenticated, authorized, and encrypted before access is granted. To minimize lateral displacement, microsegmentation and minimum permission policies are applied. Comprehensive information and analytics are equipped to detect and respond to anomalies in real time.
Verify expressly
Use Minimal Permission Access
Assume a leak
Always verify and authorize against all available data points, including user identity, location, device status, service or workload, data classification, and variances.
Restrict user access with customizable timely and sufficient access (JIT/JEA) and data protection policies to protect both data and productivity.
Minimize the impact of leaks and prevent lateral displacement by segmenting access by network, user, device, and app familiarity. Verify that all sessions are encrypted end-to-end. Use analytics to increase visibility, boost threat detection, and improve defenses.
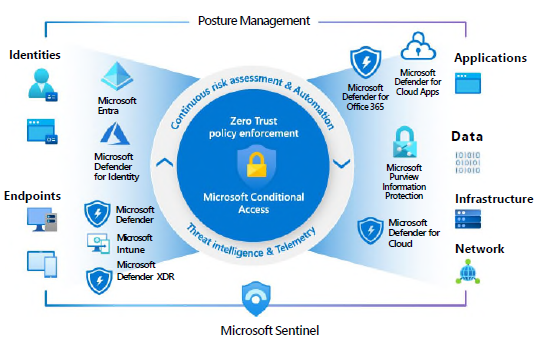
Would you like an analysis of your network or additional information?
We can help you with this.